Windows Server 2012 RDS and Windows Mobile: connection error
For whatever reason MS decided to make Windows 2012 RDS (former Terminal Services, now Remote Desktop Services) not compatible with Windows Mobile 6.x and other Windows CE 5.0 based handheld devices.
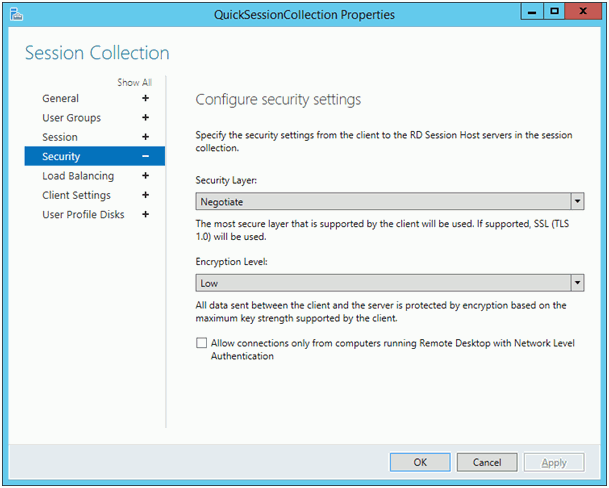
Fortunately, if you activated Remote Desktop License Server using ‘Web Browser’ method, you simply have to change the Collections Security settings and disable ‘Allow only … Network Level Authentication’ (NLA).
The following can also apply for Windows 2008 R2 Terminal Server. Check if you activate the Licensing server via “Web Browser” connection or directly. My 2008 R2 server is running OK for Windows Mobile, as a stand-alone server, with 100 licenses and activated via “Web Browser”.
But let start at the beginning.
Basic RDS setup
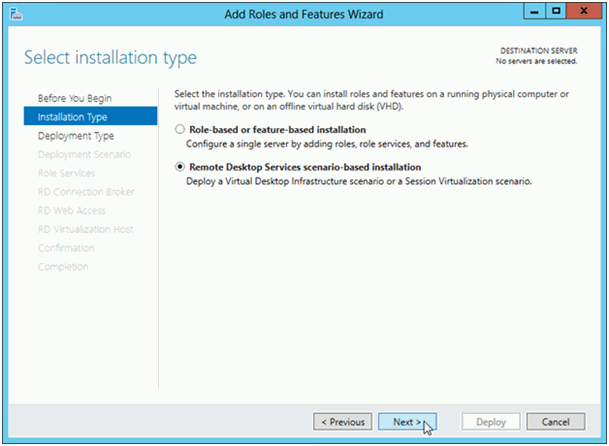
When you installed Windows 2012 Server within an existing or new Active Directory and then add the Remote Desktop Server role, you have different choices:
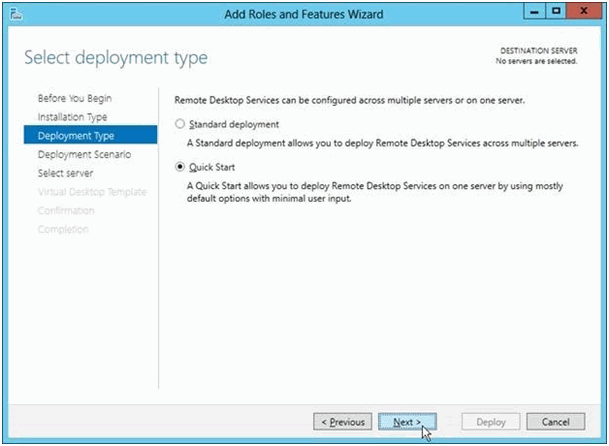
You may go on with “Remote Desktop Services scenario-based installation” and then just follow the wizard after selecting “Quick Start”.
The wizard will install everything onto one server.
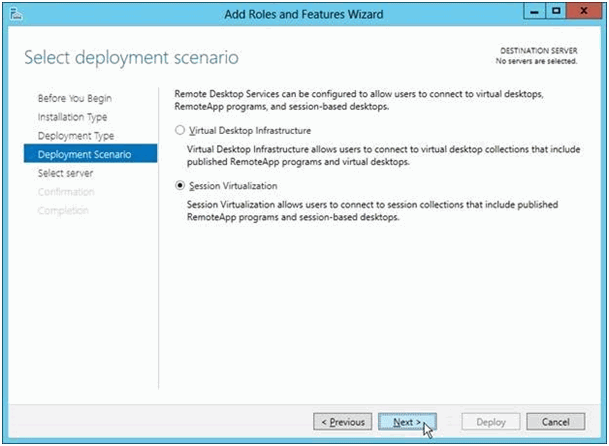
Virtual Desktop Infrastructure makes no sense for Windows Mobile clients. They do not need a full virtual windows machine based on a virtual machine. So we select “Session Virtualization”.
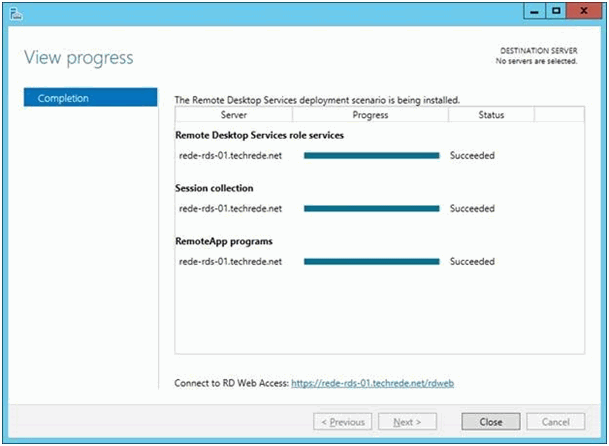
The wizard will then deploy all the services and roles and create one default “Session Collection” and “Remote Apps”. At the end you should get following screen:
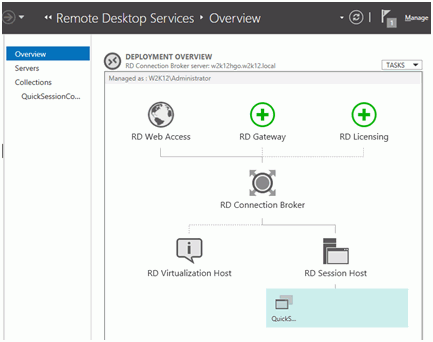
Now check the setup and look at the RDS Overview:
You see we have RD Web Access (unused by Windows Mobile but cannot be removed), no RD Gateway (not needed here), no RD Licensing (we will install that later), the RD Connection Broker, no RD Virtualization Host (as we do not provide virtual machines here) and a RD Session Host with a QuickSession Collection.
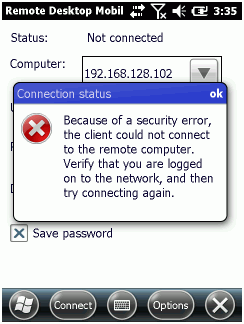
At this stage we can not connect using Windows Mobile client. The NLA setting dis-allows that and we get an error in Remote Desktop Mobile. Just change the NLA setting of the Collection and your Windows Mobile clients can connect.
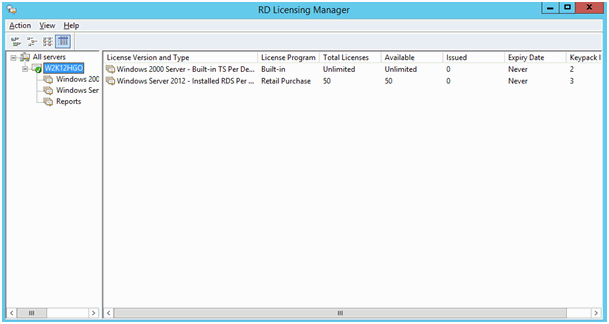
NOTE that there is no License server and we are in the 120-day trial of RDS!
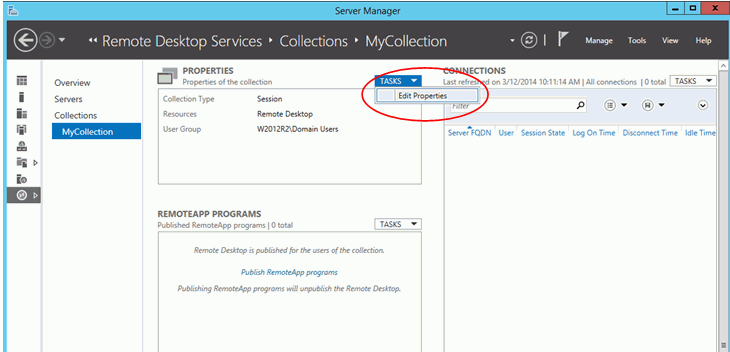
You can access the above Properties using the TASKS menu of Remote Desktop Services-Collections-CollectionName and selecting “Edit Properties”.
If there is no Collection, we can not change the setting! Windows Desktop PCs can connect to that RDS without a Collection installed. We (Windows Mobile client) need a collection to disable NLA.
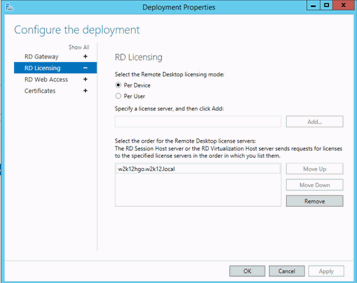
Setup Remote Desktop License Server
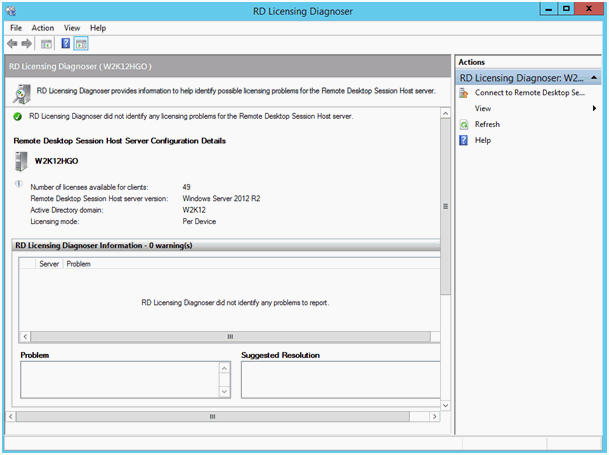
Now setup a Remote Desktop License server, activate it (or better read my later note about the activation method: see “RD License Server Activation Connection Method”) and install some CALs or DALs (licenses per User or Device). Ensure the License Manager shows your License Server without any error. And also check with RD License Diagnoser!
The licensing mode must match the general Collections properties setting:
If everything is in place and activated and licensed Windows Mobile Clients can no longer connect!
The certificates generated by the License Server are not compatible with Remote Desktop Mobile. They use 4096 bit key-length and SHA256 footprint. The certificates are stored in the registry at [HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server\RCM]. Extracted and converted these certs look like this:
Certificate: Data: Version: 3 (0x2) Serial Number: 0b:1c:04:1c:9c:74:34:af:41:3a:3c:bf:39:f5:56:bf Signature Algorithm: sha256WithRSAEncryption Issuer: C=US, ST=Washington, L=Redmond, O=Microsoft Corporation, CN=Microsoft Assurance Designation Root 2011 Validity Not Before: Mar 23 17:41:27 2011 GMT Not After : Mar 23 17:48:11 2036 GMT Subject: C=US, ST=Washington, L=Redmond, O=Microsoft Corporation, CN=Microsoft Assurance Designation Root 2011 Subject Public Key Info: Public Key Algorithm: rsaEncryption Public-Key: (4096 bit) Modulus: 00:a8:ef:ce:ef:ec:12:8b:92:94:ed:cf:aa:a5:81: 8d:4f:a4:ad:4a:ec:a5:f0:da:a8:3d:b6:e5:61:01: ... 2b:a9:44:56:83:be:b6:6e:60:b9:16:1a:e1:62:e9: 54:9d:bf Exponent: 65537 (0x10001) X509v3 extensions: X509v3 Key Usage: Digital Signature, Certificate Sign, CRL Sign X509v3 Basic Constraints: critical CA:TRUE X509v3 Subject Key Identifier: 1A:A9:53:45:33:8E:D0:6E:22:52:54:76:39:76:43:1E:FF:79:14:41 1.3.6.1.4.1.311.21.1: ... Signature Algorithm: sha256WithRSAEncryption 0b:2e:fa:54:de:11:a4:72:e4:13:1d:8b:bc:42:36:7c:fe:76: ... fa:be:02:5b:1a:c1:d9:58:66:c2:0c:b3:ce:e4:b4:ec:f4:eb: 56:4f:9a:cc:cc:b2:a0:a4
RD License Server Activation Connection Method
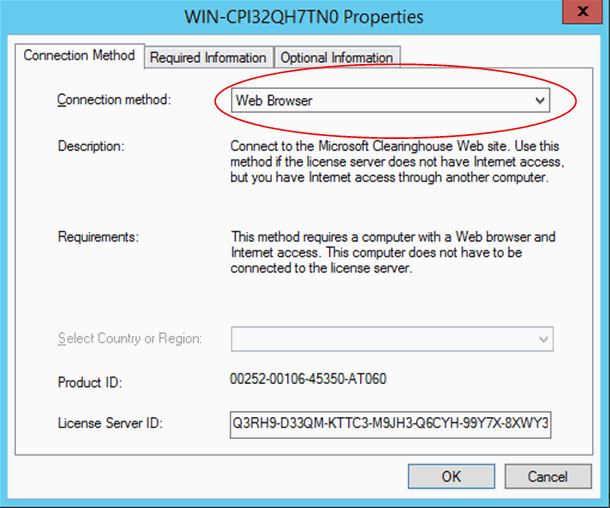
To fix that and get compatible certificates re-activate the RD Licensing Server using the Web method. In RD Licensing Manager right-click the server name and select Properties. Change the Connection Method to “Web Browser”. Close Properties with OK and again right click the server and then Advanced-Reactivate. Follow the process to reactivate the server using the web browser.
After reactivation delete the following registry keys and reboot the server!
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server\RCM o Certificate o X509 Certificate o X509 Certificate ID o X509 Certificate2
These registry keys will rebuild with lower security after reboot (see also).
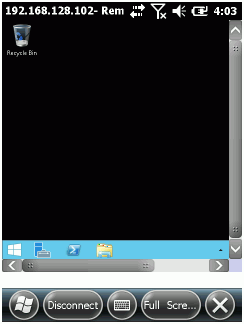
And, surprise, after reboot Remote Desktop Mobile (Windows CE5, Windows Mobile 6.x and Windows Embedded Handheld 6.5.3) can connect!
If you extract and convert the new ‘web-based’ certificates you see the difference:
Certificate: Data: Version: 3 (0x2) Serial Number: 01:9d:e7:ca:8c:9a:66:80 Signature Algorithm: sha1WithRSA Issuer: L=\x00W\x002\x00K\x001\x002, CN=\x00W\x002\x00K\x001\x002\x00H\x00G\x00O Validity Not Before: Mar 10 14:50:50 1970 GMT Not After : Mar 10 14:50:50 2049 GMT Subject: L=\x00W\x002\x00K\x001\x002, CN=\x00W\x002\x00K\x001\x002\x00H\x00G\x00O Subject Public Key Info: Public Key Algorithm: rsaEncryption Public-Key: (2048 bit) Modulus: 00:b6:7e:f2:41:23:f1:f3:cf:44:90:e7:fc:ba:3f: ... d0:51:d1:55:8c:6b:d0:f6:65:e5:c4:d2:09:1d:d0: 17:c7 Exponent: 65537 (0x10001) X509v3 extensions: X509v3 Basic Constraints: CA:TRUE, pathlen:0 1.3.6.1.4.1.311.18.8: Q.G.K.8.V.3.W.2.K.H.P.D.6.W.4.V.M.Q.2.G.3.T.H.3.K.C.8.J.W.K.W.D.M.4.Y... Signature Algorithm: sha1WithRSA 3a:1d:94:36:5d:32:12:6f:5e:e3:76:9f:cb:2b:1c:92:c2:ff: ... ac:1e:23:b2:a0:73:ff:6f:12:f8:86:24:4b:95:15:54:c0:a2: ba:05:00:e3
The key length is only 2048 bits and the security algorithm is SHA1.
If you had activated the “Web browser” Connection method before Activating the server the first time, you do not need to touch the registry and reactivate the server!
Conclusion
Windows Mobile’s Remote Desktop Mobile (RDM) application connects fine if the right certificates are generated when Activating the RD License Server. RDM will not connect, if SHA256 and 4096 bits key are used on the server. RDM does not support NLA nor SSL/TLS!
What MS says
RDS 2008, 2008R2, and 2012 will not allow connections from older RDP 5.x clients. To get around this add the following registry key to the RDS Session Host Subkey: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server\RCM Registry entry: Use512LenPropCert Data type: REG_DWORD Value: 0 or 1 This is far less secure (512bit encryption vs 2048bit), and you won't be able to take advantage of the features of later versions of the RDP protocol, but older clients will be able to connect.
What wonders me about that, is that it says ‘no support of 2048 length key’, but the key length is 2048 in my validated tests. Possibly they mean, does not support 4096 key length but 2048 (which is set with the Use512LenPropCert?).
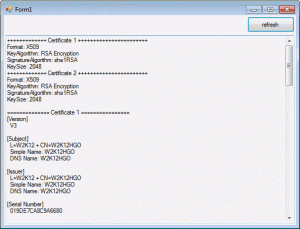
Test your installation
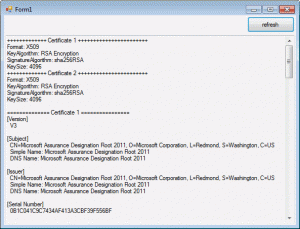
If you like to check the certificates of your installation you may use the attached demo application: “RDS2012_security”. It will just read the registry and show the certificates data.
The code (included in the attachment) just reads the registry and extracts the certification data. The data is stored binary with some extra data at the beginning. There are twelve bytes to remove to get the raw certificate (all these certs start with 0x30 0x82). So the reg might look like this:
"X509 Certificate"=hex:02,00,00,00,04,00,00,00,f1,05,00,00,30,82,05,ed,30,82,\ 03,d5,a0,03,02,01,02,02,10,0b,1c,04,1c,9c,74,34,af,41,3a,3c,bf,39,f5,56,bf,\ 30,0d,06,09,2a,86,48,86,f7,0d,01,01,0b,05,00,30,81,88,31,0b,30,09,06,03,55,\ ...
Then the tool has to remove the first 12 bytes and we get the raw data:
30,82,05,ed,30,82,\ 03,d5,a0,03,02,01,02,02,10,0b,1c,04,1c,9c,74,34,af,41,3a,3c,bf,39,f5,56,bf,\ 30,0d,06,09,2a,86,48,86,f7,0d,01,01,0b,05,00,30,81,88,31,0b,30,09,06,03,55,\ ...
Here is the simple code that does this in csharp and then initializes a new X509Certificate2 object:
const string rd_mainRegKey = @"SYSTEM\CurrentControlSet\Control\Terminal Server\RCM"
string[] _x509ValueNames = new string[] { "X509 Certificate", "X509 Certificate2" };
...
byte[] readX509Cert(string sValueName)
{
byte[] buf = null;
using (RegistryKey rk = Registry.LocalMachine.OpenSubKey(rd_mainRegKey, false))
{
byte[] bufTemp = (byte[]) rk.GetValue(sValueName);
//remove first 12 bytes
buf = new byte[bufTemp.Length - 0x0b];
Array.Copy(bufTemp, 0x0c, buf, 0, bufTemp.Length - 0x0c);
}
if(sValueName.EndsWith("2"))
_x509Certificate2=new X509Certificate2(buf);
else
_x509Certificate = new X509Certificate2(buf);
return buf;
}
Now you can even save the cert or, like the demo does, just show the key length and used algorithm.
[Download not found]




 http://www.led-mg.de
http://www.led-mg.de